<-Back to About Ciphers
Caesar
History
The Caesar cipher is one of the earliest and simplest known ciphers. It is named after Julius Caesar, the ancient Roman military general and statesman, who is believed to have used this cipher to communicate confidential military messages.
Julius Caesar would shift each letter of the plaintext by a fixed number of positions down the alphabet. For example, with a shift of 3, the letter 'A' would be encrypted as 'D', 'B' as 'E', and so on. This method allowed Caesar to send messages that could only be deciphered by those who knew the specific shift value.
The Caesar cipher served as a rudimentary form of encryption in ancient times. However, as its simplicity made it susceptible to frequency analysis attacks, it offered minimal security. Nevertheless, it played a significant role in the history of cryptography, serving as a foundation for more advanced ciphers and encryption techniques developed later.
Today, the Caesar cipher is often used as a teaching tool to introduce the concept of encryption and demonstrate the principles of shifting letters in a simple substitution cipher. It serves as a starting point for understanding more complex cryptographic algorithms.
Some quotes from online:
“The "Caesar Box," or "Caesar Cipher," is one of the earliest known ciphers. Developed around 100 BC, it was used by Julius Caesar to send secret messages to his generals in the field. In the event that one of his messages got intercepted, his opponent could not read them”.
“The Caesar Cipher is a monoalphabetic rotation cipher used by Gaius Julius Caesar. Caesar rotated each letter of the plaintext forward three times to encrypt, so that A became D, B became E, etc”.
How to it works
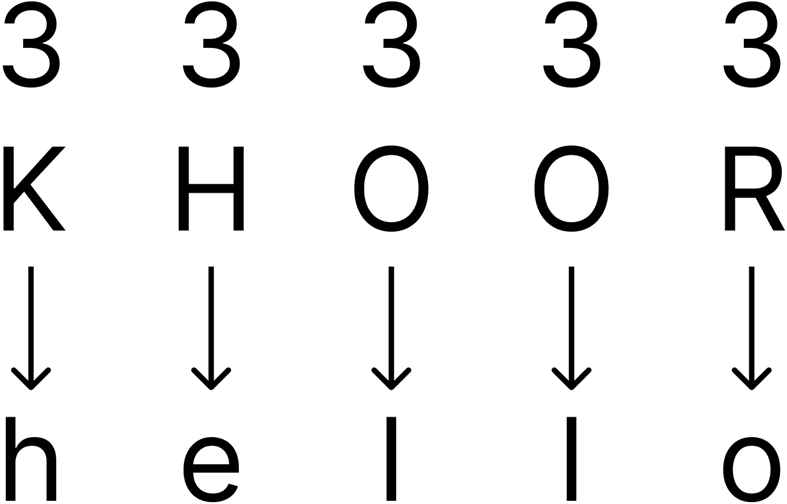
Caesar ciphers work by taking a word (plaintext), say “hello”, and moving each letter along the alphabet by a certain number (this number is the key). If the key is 3 (can be called a shift of 3), then encrypting the plaintext “hello” gives the cyphertext “KHOOR”.
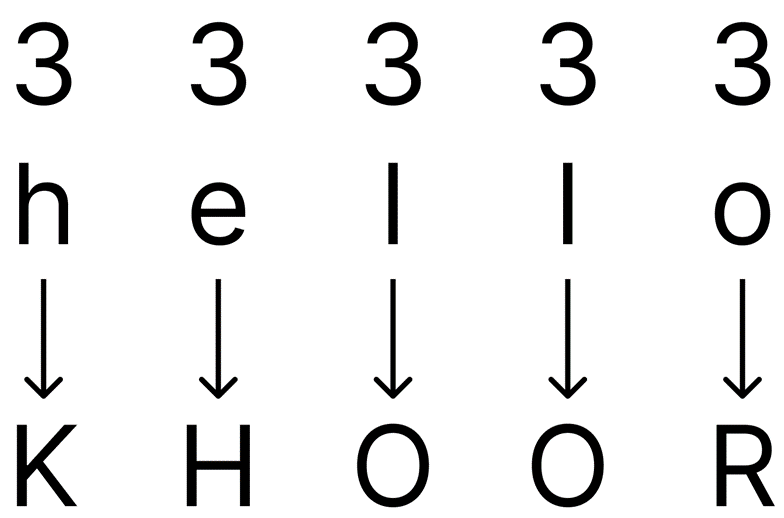
Looking at it per letter, we see that a shift of 3 moves ‘h’ to ‘K’, ‘e’ to ‘H’, ‘l’ to ‘O’ and ‘o’ to ‘R’. The key can be any number from 0 (A) to 25 (Z), noting that 26 would bring us back to the same position in the alphabet as 0; negative numbers can be used for the key e.g. a key of -1 would change the letter ‘a’ to ‘Z’, but keep in mind that 25 would also change ‘a’ to ‘Z’.
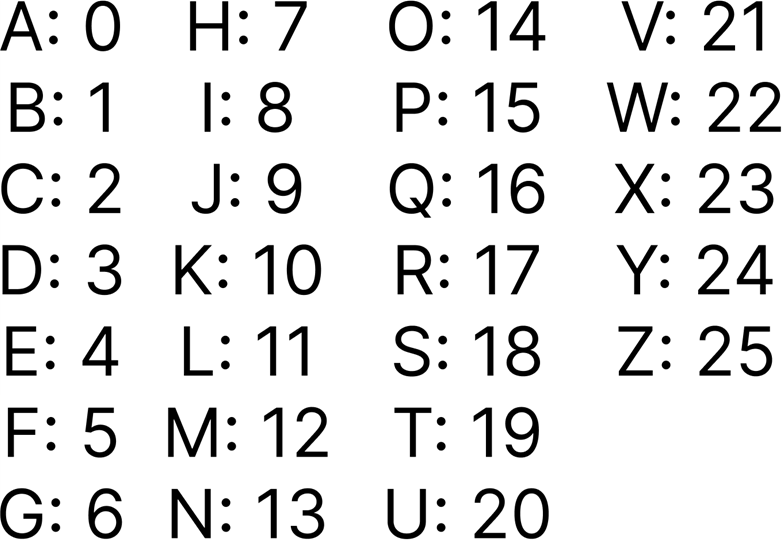
Referring to the keys with letters instead of numbers (where A is 0 to represent shift from A) can be used in a Caesar cipher, but the use of letters for a key is more useful in the Vigenère cipher, where multiple shifts occur.
In order to decipher a Caesar cipher, it is as simple as looking at the letters in the cyphertext and guessing what the key is.
Note that a key (say 3) used in encryption is different in decryption (key becomes -3), since the shifting of letters moves in the opposite direction, in order to return to the original plaintext. However, for simplicity's sake, we won't use negative keys as it is the magnitude of the shift we want to know and the direction of the shift should be/become obvious.
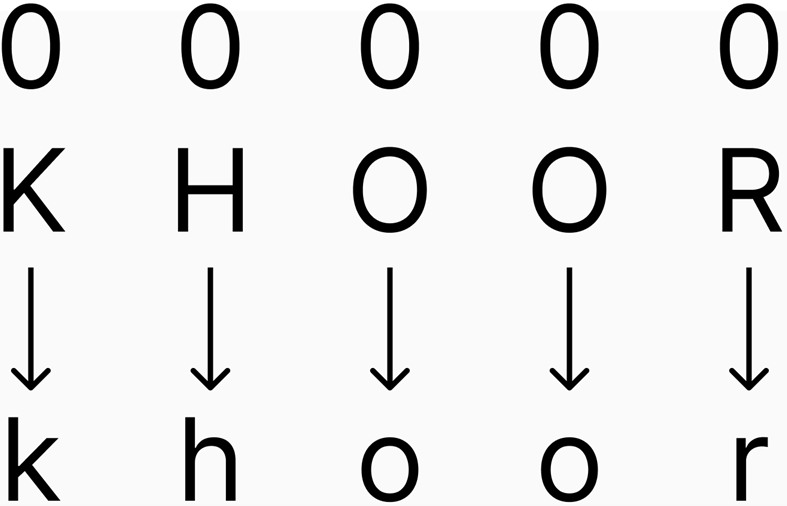
Key shift of 0:
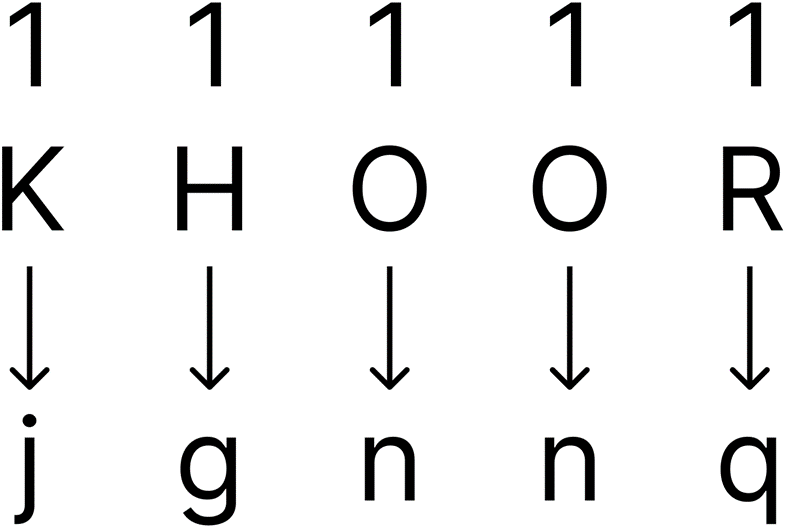
Key shift of 1:
Key shift of 2:
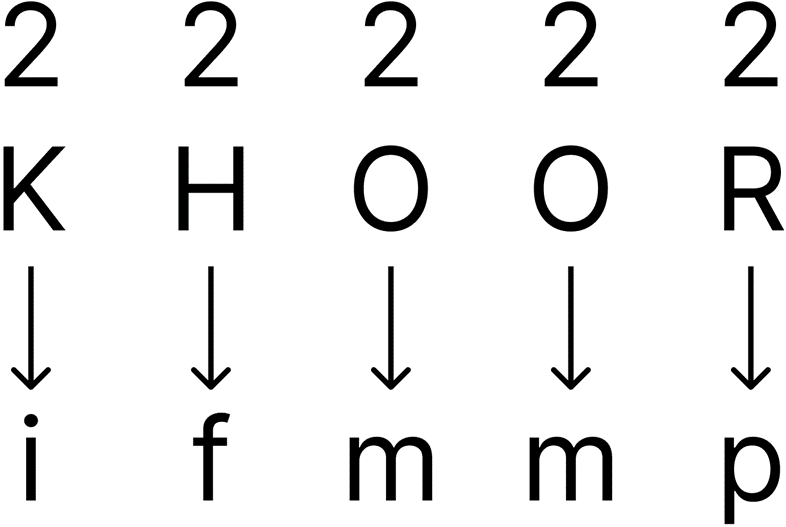
Key shift of 3:
If every letter in the cyphertext can be shifted by the same amount to form a (valid) word/plaintext, then the key has most likely been found and the discovered plaintext is correct. if a word/plaintext is formed, but the shift of each letter is different, then it has either not been deciphered correctly or a different cipher tool has been used (e.g. Vigenère cipher).
How it works (in the game)
In the user vs user game mode, Play User, one user will be the defender and one user will be the attacker each round. After each round ends the two users swap roles, so the attacker becomes the defender and the defender becomes the attacker. Each player plays at most 5 rounds as an attacker and 5 rounds as a defender (so the max number of rounds is 10), where users can earn a point each attacker round. A total of 5 points can be earned by each player and the player with the most points after 10 rounds wins. It is a draw if both players have the same number of points. Defenders and Attackers are explained below.
Defender:
The defender will be asked to make a correct plaintext (to be encrypted), a second plaintext, a key (length) and a cyphertext. The cyphertext will be an encryption of the correct plaintext and thus it’s important that the defender states what key was used (the number the letters were shifted by) in order to create the cyphertext, that way the computer can confirm whether the cyphertext is acceptable (ensuring the rules are maintained). Note that the second plaintext will not be encrypted and should be the same length as the correct plaintext, that way the attacker will consider that it may be the correct plaintext.
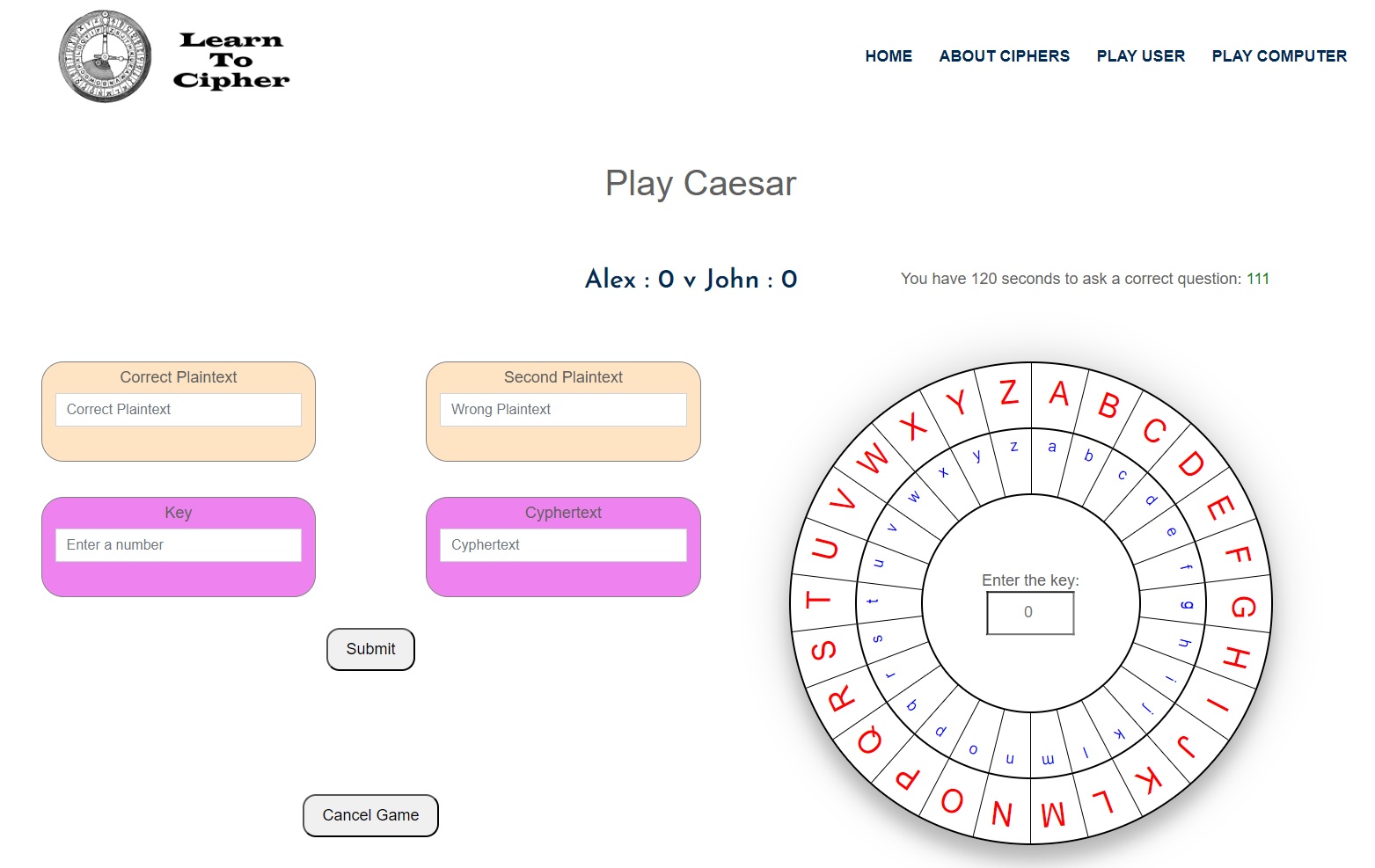
The cipher wheel on the right can be used by the defender to create the cyphertext, by changing the key (the number) in the centre of the wheel and thus the defender can observe letter by letter how the correct plaintext encrypts into the cyphertext. The 'Key' box is where the defender tells the computer what the key is, where as the key in the cipher wheel is just a visual assistance for the defender, so remember to type the key into the 'Key' box.
Note: there is a 4-minute timer to make a question, so if the defender fails to submit a question (correct plaintext, second plaintext, key and cyphertext) within the time limit then a point is given to the attacker, otherwise the defender could simply not submit a question and deny the attacker the opportunity to earn a point. Keep in mind that if the cyphertext is wrong (based on the correct plaintext and the key) then the game will notify the user and correcting the cyphertext may take time, so bare this in mind.
After the defender submits their question, the defender then waits for the attacker to answer the question, with the words “Please wait for your opponent to answer” in green.
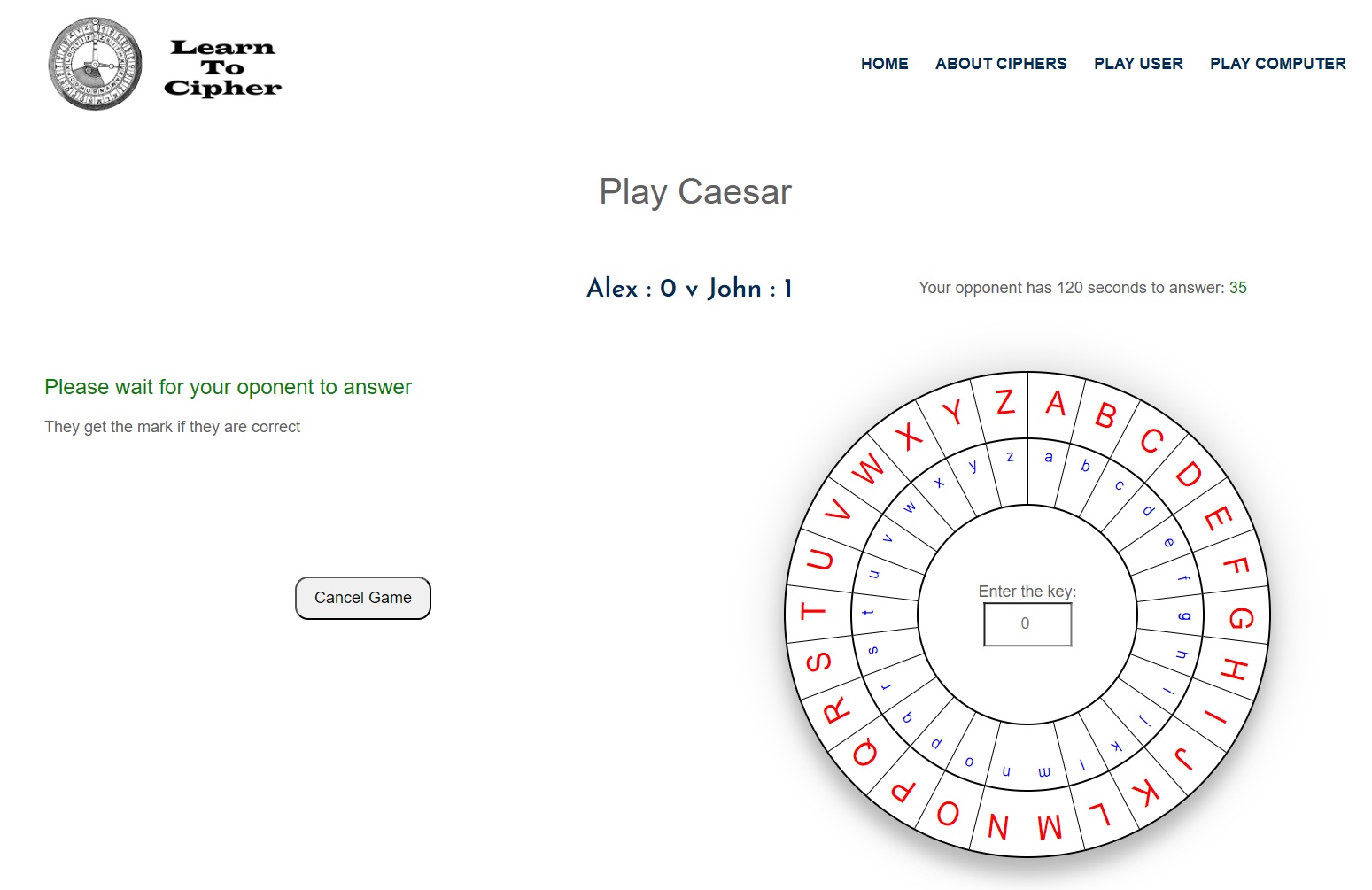
If the attacker guesses correctly they receive a point, otherwise no points given. Then the two users switch roles between defender and attacker.
Attacker:
Initially the attacker must wait for the defender to make a question, where they will see a waiting screen with the words “Please wait for your opponent to ask a question”.

Once the defender has submitted their question, the attacker is then asked to guess or work out which of the plaintexts has been encrypted to form the cyphertext, where the screen looks like this:
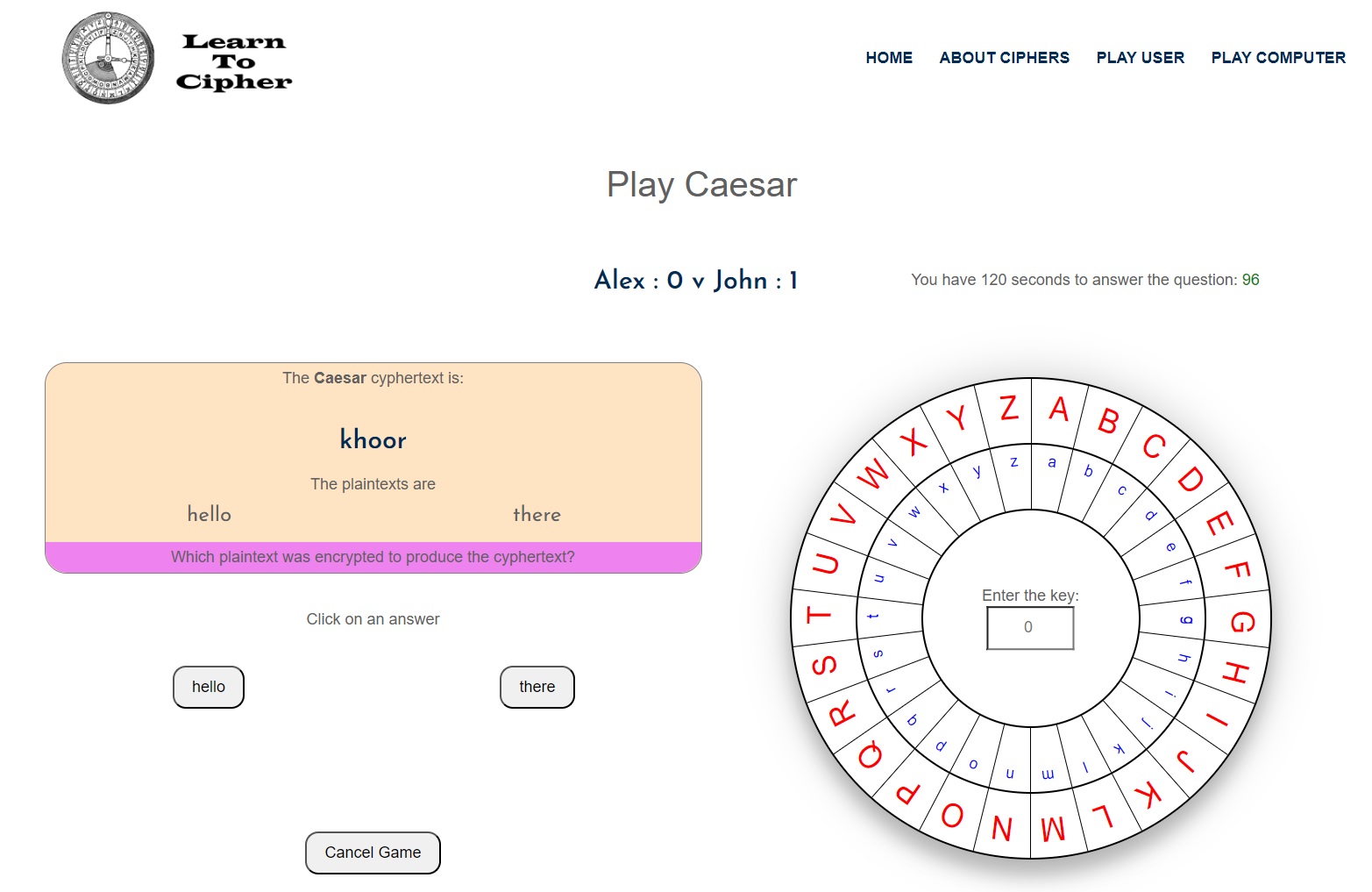
The attacker can either guess by looking at the two plaintexts or can use the cipher wheel on the right-hand-side of the screen to decipher the cyphertext, where the cipher wheel helps the attacker observe if all the letters in a word are shifted by the same number or not.
Note: in a Caesar cipher the user only really needs to compare the first two letters in the plaintext with the first two letters in the cyphertext, since the letter shift (key) will be the same across all letters and thus if the first two letters have the same shift then the user has found the correct plaintext.
The attacker confirms their answer by clicking on the plaintext they believe is the correct answer. If the attacker guesses correctly they receive a point, otherwise no points given. There is a 4-minute timer for the attacker to confirm their answer, where if they don’t answer in time then they don’t receive a point. After answering (or not answering), the two users switch roles between defender and attacker.
In the user vs computer game mode (Play Computer), it is the same as the user vs user game mode, except the computer is always the defender and the player is always the attacker. Since the player is always the attacker, all they need to do is answer the correct plaintext.
<-Back to About Ciphers