<-Back to About Ciphers
Vigenère
History
The Vigenère cipher, invented by Giovan Battista Bellaso in 1553 and later popularized by Blaise de Vigenère in 1586, is a polyalphabetic substitution cipher that improved upon the security of simple substitution ciphers.
The Vigenère cipher uses a keyword or passphrase to determine the shifting of letters in the plaintext. Each letter in the keyword corresponds to a specific shift value. By repeating the keyword for the length of the plaintext, a series of different Caesar ciphers is created. This makes the Vigenère cipher more resistant to frequency analysis attacks.
For centuries, the Vigenère cipher remained unbroken and was considered unbreakable until the 19th century when the Kasiski examination and Friedrich Kasiski's discovery of repeating patterns in the ciphertext helped break the cipher.
The Vigenère cipher played a significant role in the history of cryptography and served as a precursor to more complex encryption techniques. It introduced the concept of using a keyword or passphrase to enhance the security of substitution ciphers. Today, the Vigenère cipher is still studied as a classic example of a polyalphabetic substitution cipher and provides insight into the evolution of cryptographic methods.
Some quotes from online:
“The cipher was invented in 1553 by the Italian cryptographer Giovan Battista Bellaso but for centuries was attributed to the 16th-century French cryptographer Blaise de Vigenère, who devised a similar cipher in 1586”.
“Charles Babbage is known to have broken a variant of the cipher as early as 1854 but did not publish his work. Kasiski entirely broke the cipher and published the technique in the 19th century, but even in the 16th century, some skilled cryptanalysts could occasionally break the cipher”
How it works
Vigenère ciphers work by taking a word, say “hello”, and moving (shifting) individual letters in the word along the alphabet by certain numbers (depending on the key). The key is a certain number of letters which each represent the shifts (A represents 0 shift, E 4 shift, M 12 shift, etc) and the order of the letter in the key dictates the order they affect the word/plaintext. If the key is “AND” and the word is “hello”, then encrypting the word gives the cyphertext “HROLB”. Looking at it per letter, we see that ‘h’ and the second ‘l’ are shifted by A (shift 0) giving ‘H’ and ‘L’ as they were, ‘e’ and ‘o’ are shifted by N (shift 13) giving ‘R’ and ‘B’ and lastly the first ‘l’ is shifted by D (shift 3) giving ‘O’.
If it’s not obvious which letter in the key affects which letter in the word, let's me represent it differently and go step by step:
Step 1:
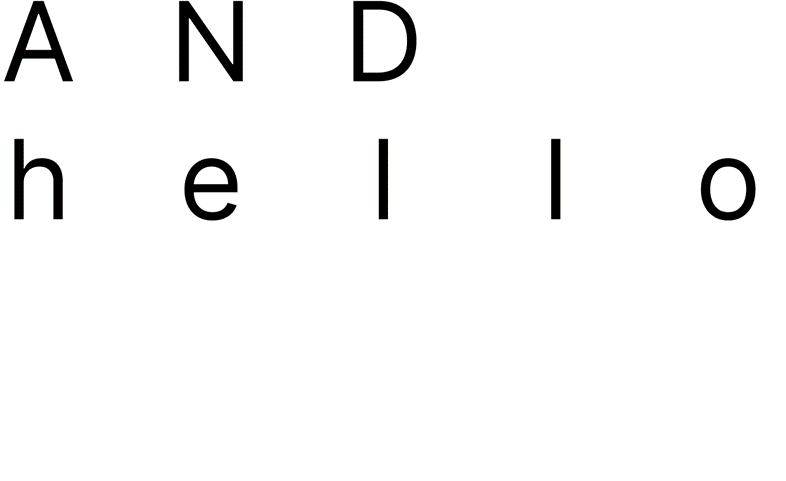
Here the letters in the key (A, N and D) line up with the first three letters in the word “hello”. The idea is to line up the key (where its length can be equal or less than the length of the word) with the word, such that it’s clear what letter in the word is affected by each letter in the key.
Step 2:

When the key is shorter than the word, the letters in the key are repeated (in order) along the word, thus all the letters in the word now have a letter from the key.
Step 3:
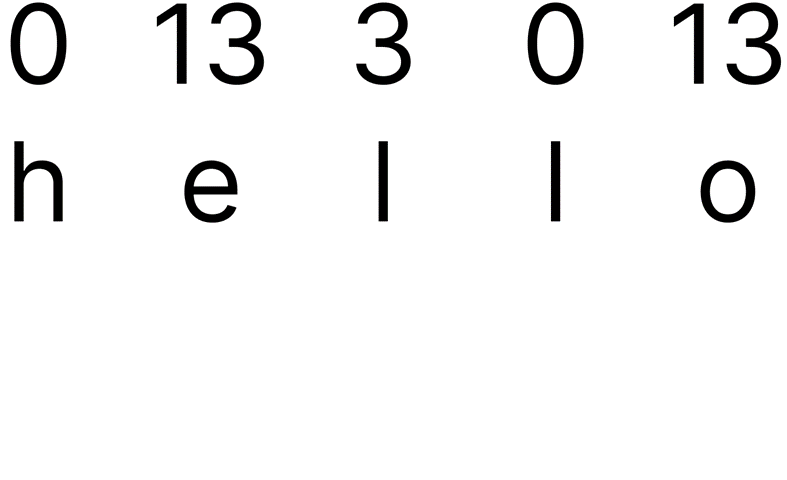
The letters in the key have been changed into their shifts (A is 0, N is 13, D is 3). Step 3 is purely for explanatory purposes, but writing down or noting each shift is good practice.
Step 4:
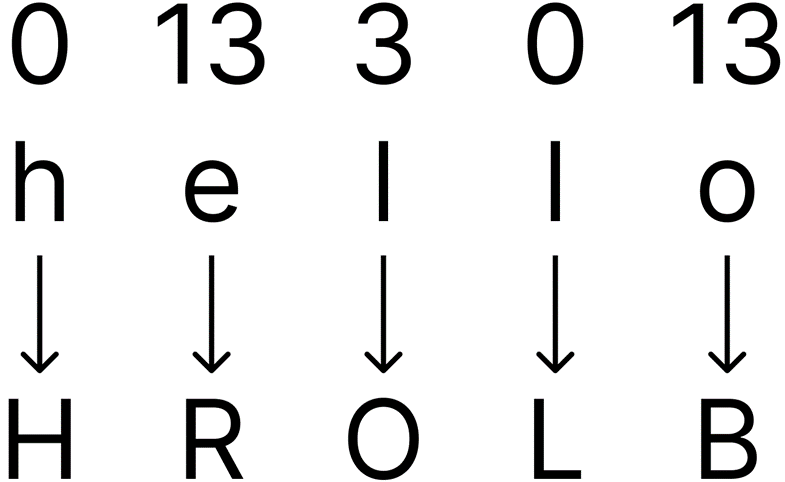
Now the encryption has been done, where the arrows show what letters are produced to form the cyphertext.
In order to decipher a Vigenère cipher, each letter in the cyphertext needs to be examined for what the shift could be. This is of course tedious and it may be difficult to determine correctly what each shift is, but there is a hint to look out for. As stated already, the key can be equal or less than the word (and cyphertext) so looking out for which letters in the cyphertext may have the same shift is good to note.
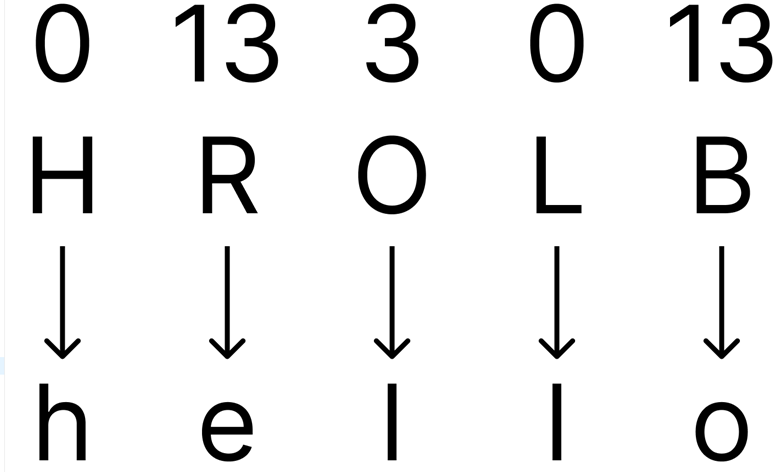
In the “hello” example, the key is 3 letters long and thus the 1st letter is shifted by the same amount as the 4th letter:
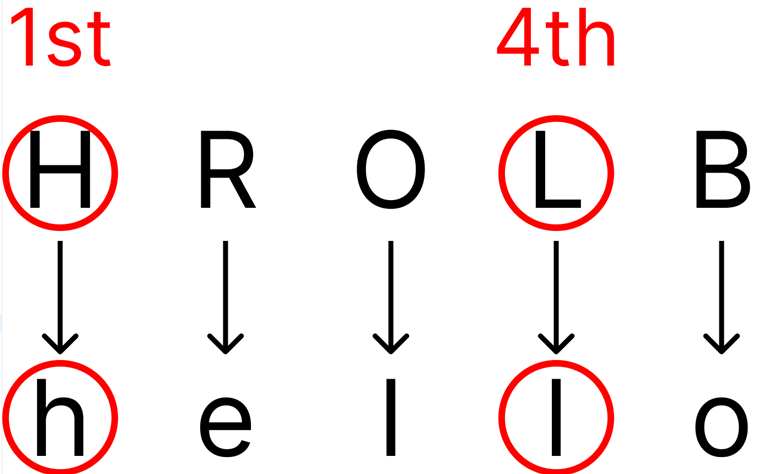
The 2nd letter is shifted by the same amount as the 5th letter:
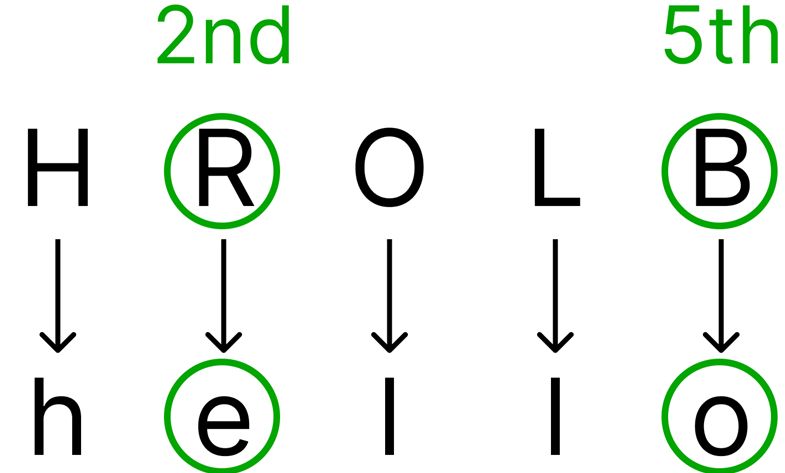
Lastly, the 3rd letter would be shifted by the same amount as the 6th letter (but not in this example, since the plaintext only has 5 letters):
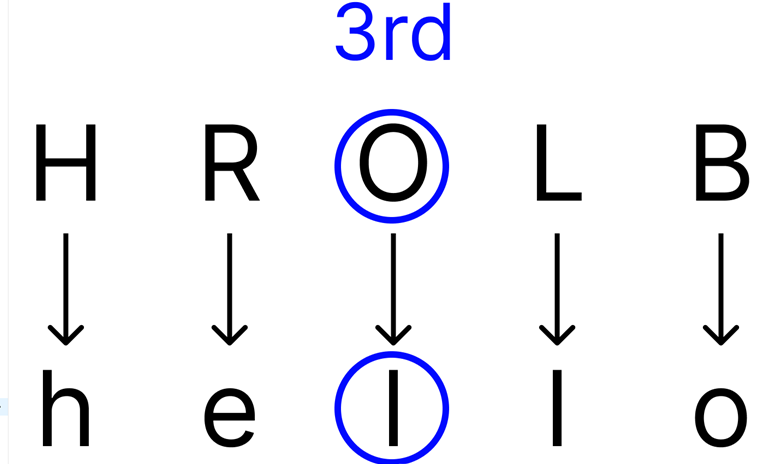
Different lengths of keys dictate which letters in the word have been shifted by the same amount to form the cyphertext. There are methods to decipher a Vigenère cipher, but these won’t be covered as they won’t be necessary for you to answer a Vigenère cipher question in the game (since the game will always use a key of 3).
How it works (in the game)
In the user vs user game mode, one user will be the defender and one user will be the attacker each round. After each round the two users swap roles, so the attacker becomes the defender and the defender becomes the attacker. Each player plays at most 5 rounds as an attacker and 5 rounds as a defender (so the max number of rounds is 10), where users can earn a point each attacker round. A total of 5 points can be earned by each player and the player with the most points after 10 rounds wins. It is a draw if both players have the same number of points. Defenders and Attackers are explained below.
Defender:
The defender will be asked to make a correct plaintext (to be encrypted), a second plaintext, a key (of 3 letters) and a cyphertext. The cyphertext will be an encryption of the correct plaintext and thus it’s important that the defender states what key was used (3 letters to indicate 3 shifts) in order to create the cyphertext, that way the computer can confirm whether the cyphertext is acceptable (ensuring the rules are maintained).
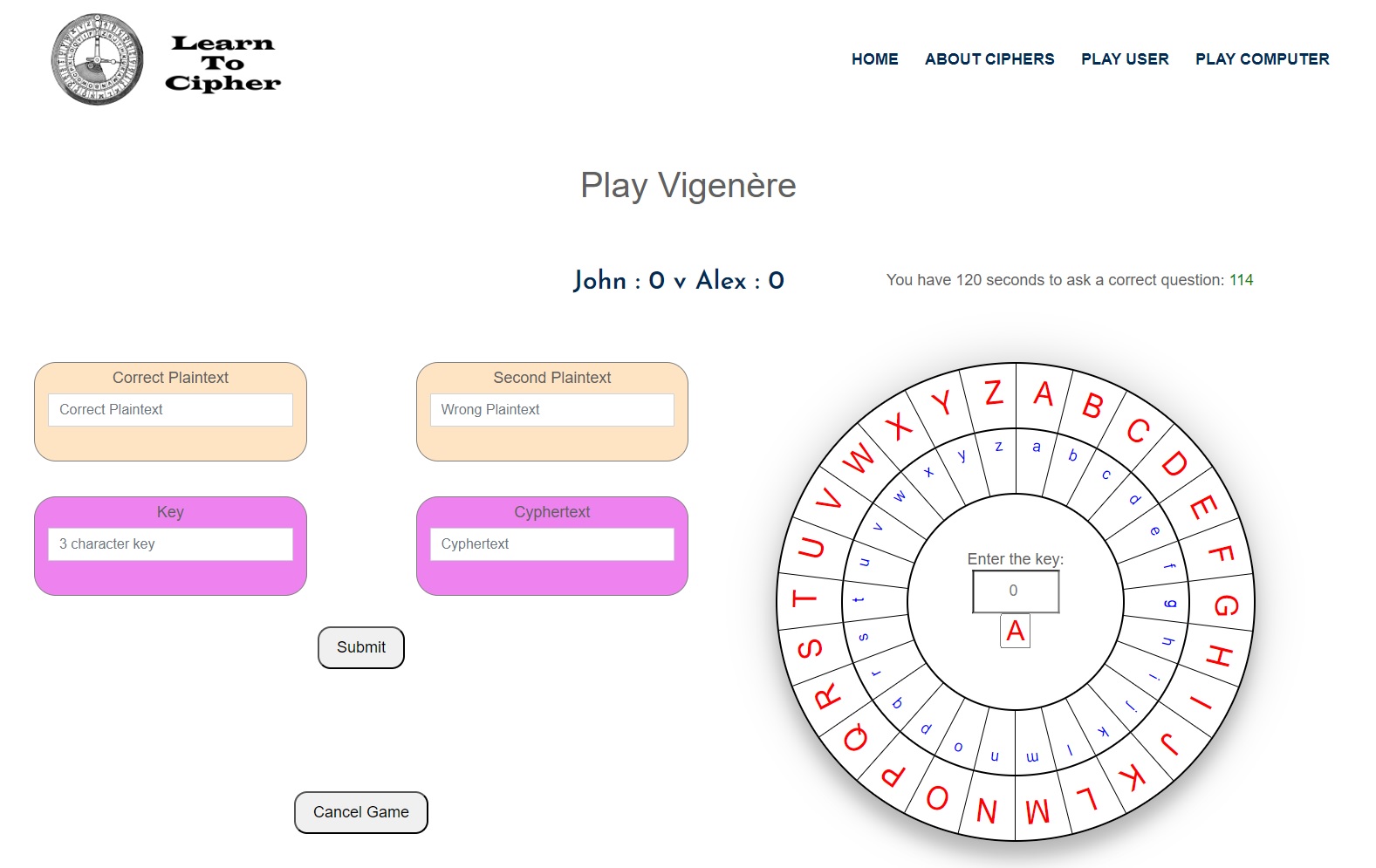
The cipher wheel on the right can be used by the defender to create the cyphertext, by changing the key (the number AND letter underneath) in the centre of the wheel and thus the defender can observe letter by letter how the correct plaintext encrypts into the cyphertext. In a Vigenère cipher wheel, the wheel will have to be aligned for each letter/shift in the key, in other words each of the 3 letters in the key will be used to rotate the Vigenère cipher wheel. The 'Key' box is where the defender tells the computer what the key is (of 3 letters), where as the key in the cipher wheel is just a visual assistance for the defender, so remember to type the key into the 'Key' box.
Note: there is a 4-minute timer to make a question, so if the defender fails to submit a question (correct plaintext, second plaintext, key and cyphertext) within the time limit then a point is given to the attacker, otherwise the defender could simply not submit a question and deny the attacker the opportunity to earn a point. Keep in mind that if the cyphertext is wrong (based on the correct plaintext and the key) then the game will notify the user and correcting the cyphertext may take time, so bare this in mind.
After the defender submits their question, the defender then waits for the attacker to answer the question, with the words “Please wait for your opponent to answer” in green.
If the attacker guesses correctly they receive a point, otherwise no points given. Then the two users switch roles between defender and attacker.
Attacker:
Initially the attacker must wait for the defender to make a question, where they will see a waiting screen with the words “Please wait for your opponent to ask a question”.
Once the defender has submitted their question, the attacker is then asked to guess or work out which of the plaintexts has been encrypted to form the cyphertext, where the screen looks like this:
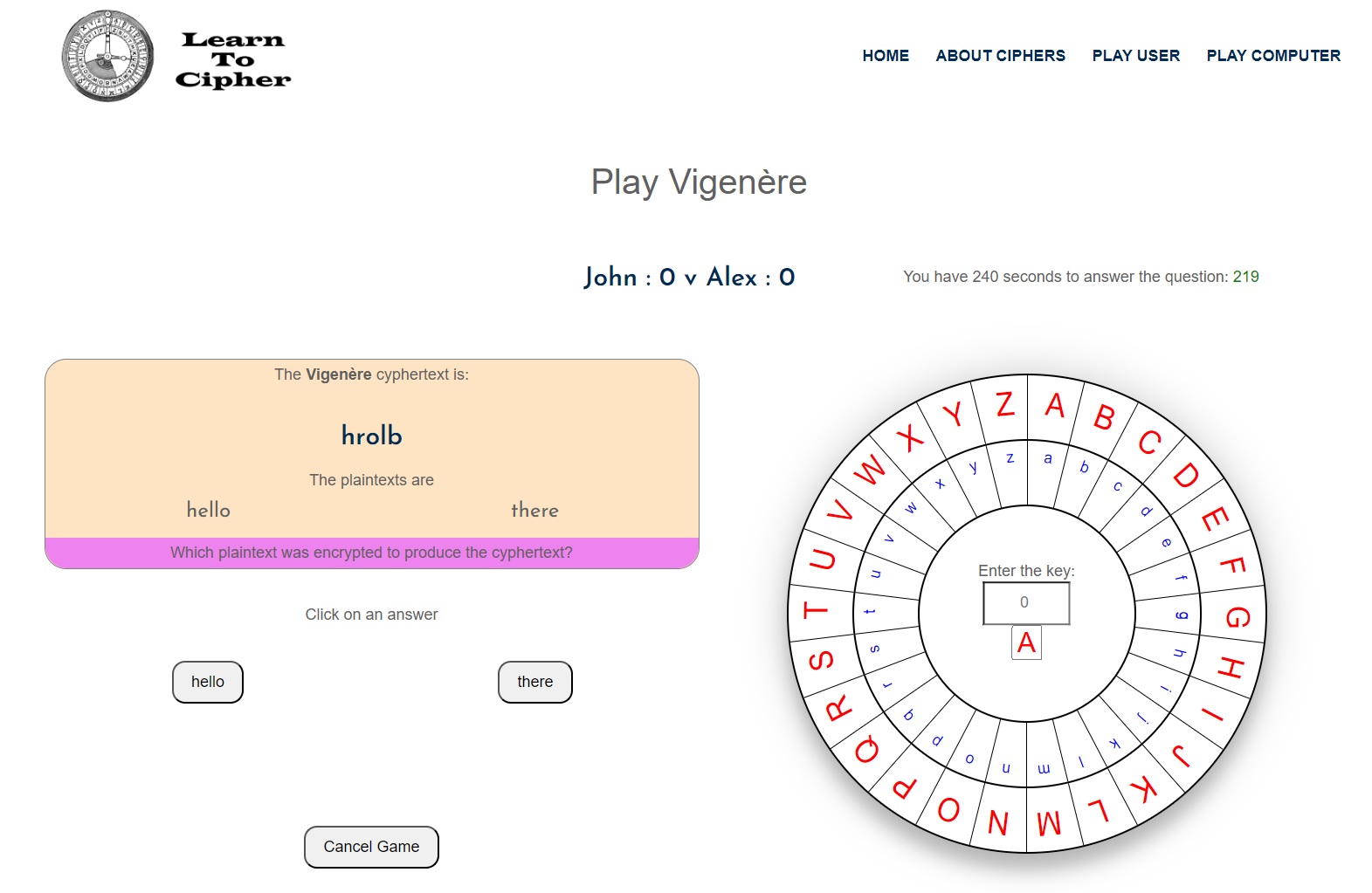
The attacker can either guess by looking at the two plaintexts or can use the cipher wheel on the right-hand-side of the screen to decipher the cyphertext, where the cipher wheel helps the attacker observe the shifts between the plaintexts and the cyphertext.
Note: in a Vigenère cipher the user only really needs to compare the 1st and 4th letters in the plaintext with the 1st and 4th letters in the cyphertext, due to the fact that the length of the key is always 3 and thus the letter shift will be the same for the 1st and 4th letters, so if the 1st and 4th letters have the same shift then the user has found the correct plaintext.
The attacker confirms their answer by clicking on the plaintext they believe is the correct answer. If the attacker guesses correctly they receive a point, otherwise no points given. There is a 4-minute timer for the attacker to confirm their answer, where if they don’t answer in time then they don’t receive a point. After answering (or not answering), the two users switch roles between defender and attacker.
In the user vs computer game mode, it is the same as the user vs user game mode, except the computer is always the defender and the player is always the attacker. Since the player is always the attacker, all they need to do is answer the correct plaintext:
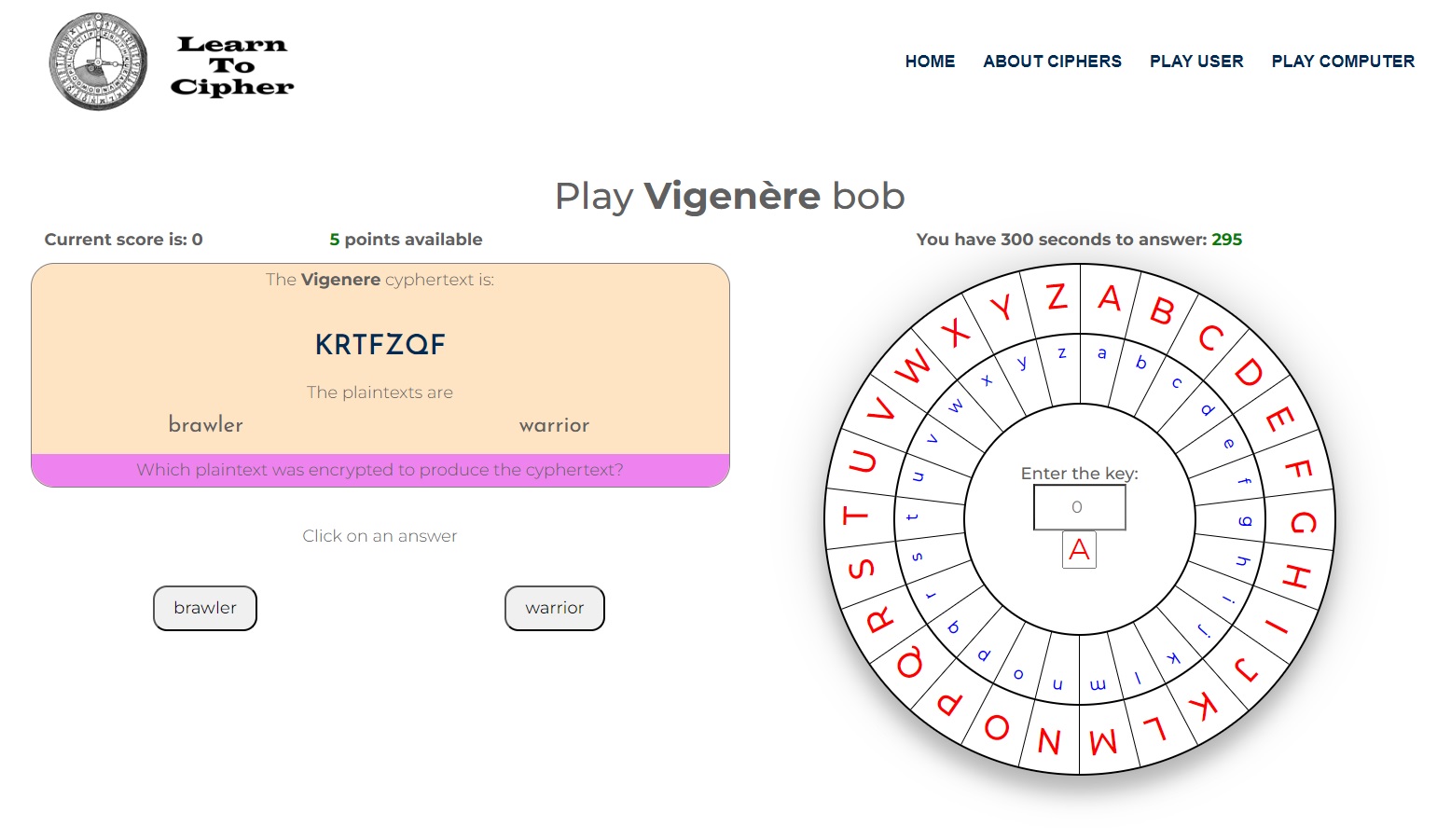
<-Back to About Ciphers