<-Back to About Ciphers
Columnar Transposition
History
Columnar transposition cipher is a type of transposition cipher that rearranges the plaintext by writing it in a grid of fixed width and then reading it out column by column. Its exact origin and early history are not well-documented.
The use of transposition ciphers, including columnar transposition, gained prominence in the 19th and 20th centuries during periods of increased interest in cryptography. They were often employed by military and intelligence organizations to protect sensitive information.
Columnar transposition gained attention during World War I when it was used by both the Allies and the Central Powers. It offered a relatively simple method to obscure the message structure and make cryptanalysis more challenging. However, with advancements in computational power and cryptanalysis techniques, columnar transposition became less secure over time.
Today, columnar transposition serves as an educational example of a classical transposition cipher and is often used in puzzle-solving, cryptography courses, and recreational cryptography. It provides insights into the historical development of cryptographic techniques and the importance of transposition ciphers in the field of cryptography.
Columnar transposition ciphers are fairly complicated ciphers and many of the most complicated ciphers to date have columnar transpositions integrated into them. For example, the double columnar transposition cipher was used in world war 2 by the US army and other nations.
Some quotes from online:
“Columnar transposition continued to be used for serious purposes as a component of more complex ciphers at least into the 1950's”.
“A variant form of columnar transposition, proposed by Émile Victor Théodore Myszkowski in 1902, requires a keyword with recurrent letters”.
“The Columnar Transposition Cipher is a type of transposition cipher, also known as a row column transposition cipher”.
“During World War II, the double transposition cipher was used by Dutch Resistance groups, the French Maquis and the British Special Operations Executive (SOE), which was in charge of managing underground activities in Europe.[2] It was also used by agents of the American Office of Strategic Services[3] and as an emergency cipher for the German Army and Navy”.
“Until the invention of the VIC cipher, double transposition was generally regarded as the most complicated cipher that an agent could operate reliably under difficult field conditions”.
How it works
Columnar transposition ciphers can be quite complicated in how they work, so an example will be used to explain how to encrypt a sentence (called a plaintext) into a cyphertext. Let’s use the plaintext “use the keyword to solve this” and arrange it into columns, such that it can be read from left to right, top to bottom:
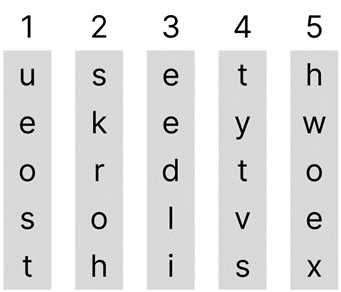
As shown, the plaintext “use the keyword to solve this” has been placed into 5 columns. An ‘x’ has been added as a ‘filler’ since the plaintext “use the keyword to solve this” has 24 letters but there are 5 columns containing 5 letters each (it’s a 5x5 grid that needs 25 letters) so an ‘x’ has to be added to the fifth column as to not leave blank areas. The plaintext could have been placed into more or less than 5 columns, but this would have resulted in a different cyphertext and key, as well as the number of rows and the number of fillers ‘x’ being different. Each column has been marked from 1 to 5, as shown above each column in the picture, to keep track of each column and help identify how the key has been used to encrypt the cyphertext. The key is what dictates the way in which the columns are moved about. This can be as simple as the key being “1 4 2 5 3” which would change the order of the columns to match the numbers in the key; the key can be a word such as “bread” and the resulting order is determined by the order that each letter in the word comes in the alphabet, so “bread” would be “2 5 4 1 3” since the letters in “bread” come in the alphabet as ‘a’, ‘b’, ‘d’, ‘e’ and ‘r’. By applying the key “1 4 2 5 3” to our plaintext (the columns) we get:
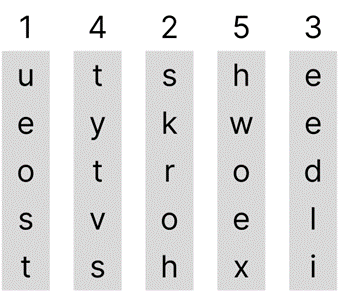
Now that the key has been applied to the columns, we now have our cyphertext which is written as:
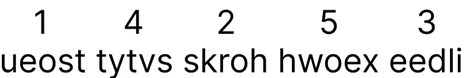
This is a 5-word sentence using the 5 letters in each column to form each word in the cyphertext. Note that the numbers are just to clarify which column each of the letters comes from, you would defintely not keep them in the cyphertext (unless you want the enemy/attacker to have your key).
In order to decipher a columnar transposition cipher, place the cyphertext back into columns. The cyphertext will always be a certain number of words (which determines number of columns), all with the same number of letters (determines number of rows). Let's use the same cyphertext produced from the encryption above:
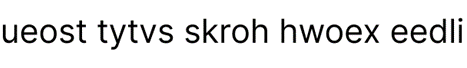
We know from the encryption from above that the order “1 4 2 5 3”, but how would we normally work out what the key is?
The solution is quite simple: move the columns about until a coherent sentence forms. This is quite a tedious process to do on paper, since writing out the columns over and over again until you find the correct order can be time consuming, but once a coherent sentence has been found then the plaintext has been found and the order (key) has been guessed correctly.
Note: In the game, an interactive tool is provided that makes rearranging the columns more convenient, so there’s no need to scribble on paper and panic over deciphering the cyphertext in time.
How it works (in the game)
In the User vs Computer game mode, the user is provided with a cyphertext containing N number of jumbled words and each letter is M letters long, which from this we can see in the interactive tool on the right that there are N number of columns and they are M letters (rows) long.
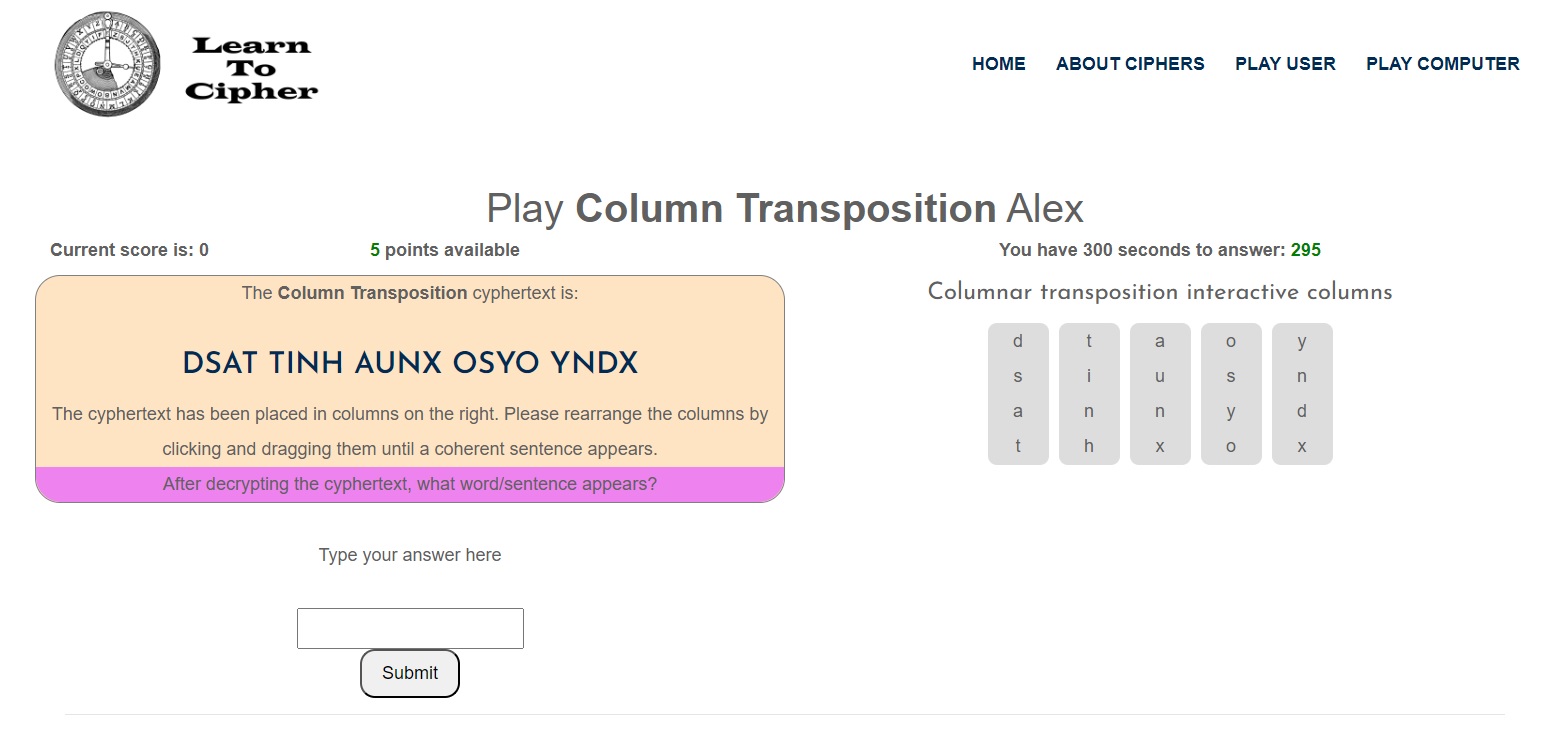
In order to decipher the cyphertext, use the interactive tool by moving the columns about until a coherent sentence forms.
Note: an easy way to confirm the position of some of the columns is to the look at the bottom row and observe the number of ‘x’s, since ‘x’ is used as a filler letter during encryption. In other words, move every column ending with an ‘x’ to the right and every other column to the left, which should reduce the time it takes for you to find the correct order (key) for the columns.
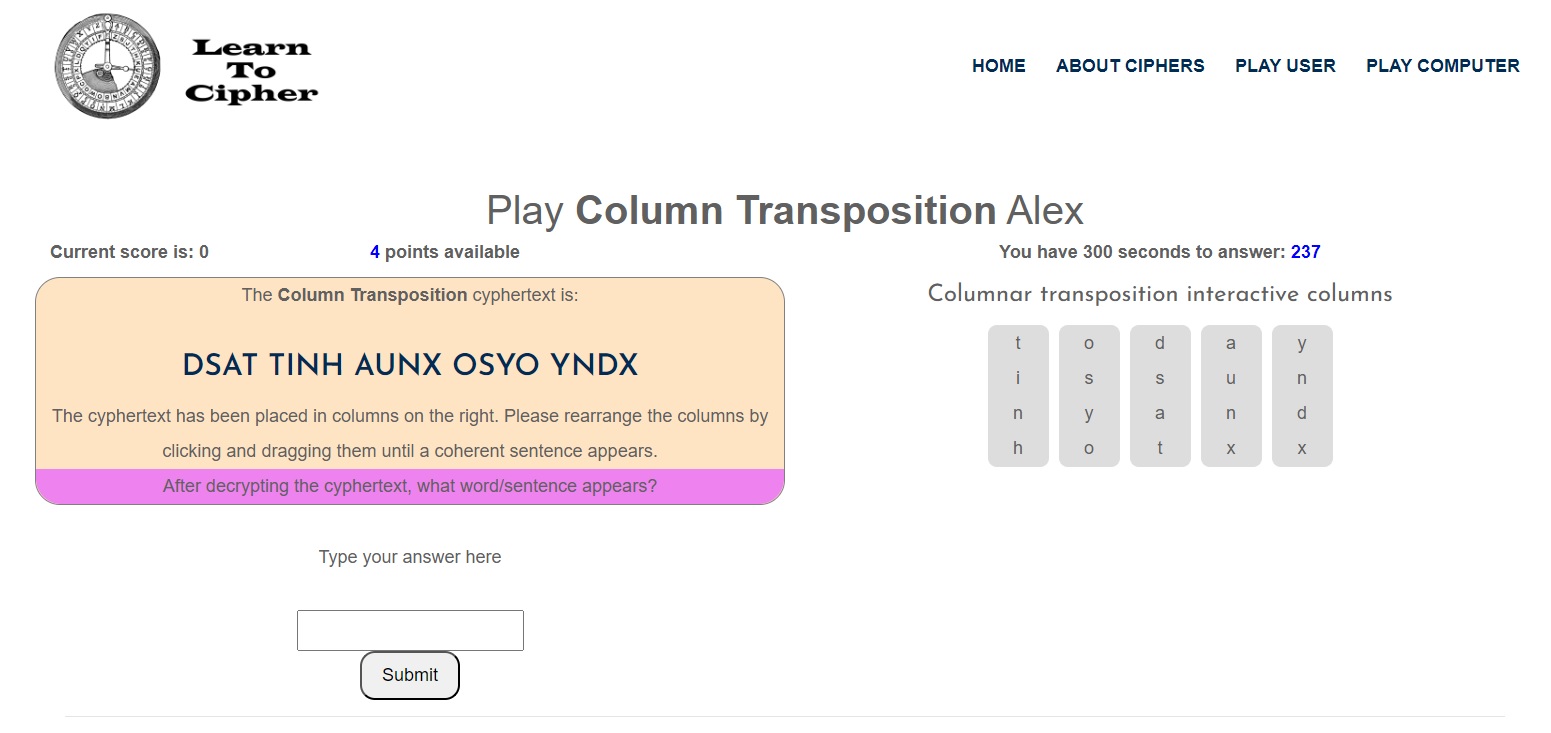
Here we see that from the cyphertext “DSAT TINH AUNX OSYO YNDX" is decrypted to form the plaintext “today is sunny and hot”. Remember that the filler 'x's are not included in the plaintext. Now you type the plaintext into the answer box and click submit.
<-Back to About Ciphers